In the world of the Internet, the security of computer systems is the basic principle for the continuity of any business.
Many powerful companies use firewall, antivirus, anti spam, etc. systems to protect the system; but very few of them use IDS (Intrusion Detection System).
What is IDS?
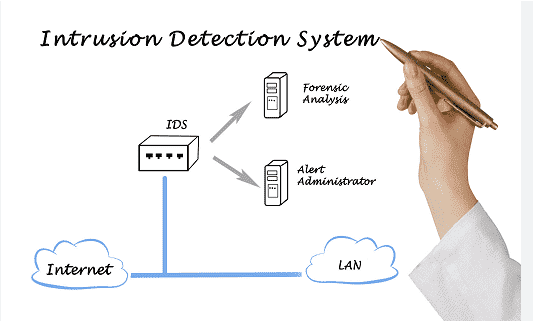
IDS is a device or application that is used to control all network traffic, and notify the system administrator when unauthorized attempts or system access is made.
Unlike the Firewall that sets up a protective barrier, or wall to prevent hackers from penetrating the system, IDS focuses on monitoring internal traffic and identifying suspicious access or virus activity on the network.
IDS systems solutions use Signature-based detection, which compares traffic with the database that attacks or attack techniques are based on. It simply detects suspicious activity, revealing deficiencies or weaknesses that a computer system may have.
Why do we need an IDS system?
We need an IDS system because, as soon as an attack on the network starts, of the Social Engineering type, for example, the firewall system cannot detect it. This is done by the IDS, which captures suspicious traffic and network accesses, notifying the relevant IT Security staff.
When we use IDS, we must keep in mind that in addition to the suspicious traffic that it analyzes, we may also have some false signals, it is the responsibility of IT Security to decide what action to take. So IT Security must know this type of system well, so as not to be alarmed if any false negative notification can come from a simple user.
